A Song of Bluetooth chinese lamp & excruciating reverse engineering - Day 2
2019-03-05We need to go deeper
At this point I knew that I needed to do what all the cool kids are doing nowadays and totally buy IDA Pro, but I wanted to try and go on the open source path. So I again turned to Google and found radare2, and even better I found Cutter, an experimental GUI for radare2.
I should also point out that I was reversing the x86 version of the packer because I am just more accustomed to x86 assembly. Sorry not sorry.
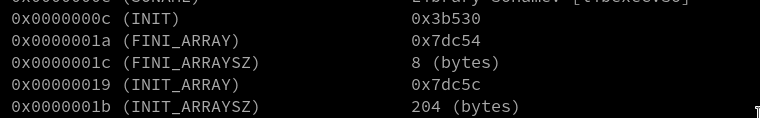
Readelf -a never fails to amaze me and it found multiple entrypoints:
Fired Cutter up, opened x86/libexec.so, added a symbol to +0x3b530 and started looking around.
Everything except the bytes around that function look gibberish, and that usually is pretty promising. I spark with joy recognizing some INT 0x80 after mov eax, 9 (mmap).
I see that Cutter has a big play button, and after sprinkling breakpoints on some calls I click on it. Cutter suddenly switches to an horrible black theme and push instructions don't seem to work (they literally don't put the value on the stack).
At the time of writing Cutter is considered beta software. Maybe learning radare2 cli can help?
I spend the rest of the evening reading the radare2 official book (it looked very cool) and already being a vim user I felt quite at home.
But I was still having problems with actually running the function.
I decided to chat about this project with a dear friend of mine that works in the cybersecurity field and he recommended Giovanni Rocca's blog.
After reading Giovanni's blog (this particular article to be precise) I am convinced I need to use frida and that, in general, I must continue my dynamic analysis on a real phone. Time to root my OnePlus 6. And I need to do this on Windows. Darn it.
TL;DR for the day: Wasted an evening learning radare2, ended up using Frida AND needed to use the worst OS I could end up using.